Pawn Storm Abuses OAuth In Social Engineering Attacks
Por um escritor misterioso
Last updated 23 maio 2024
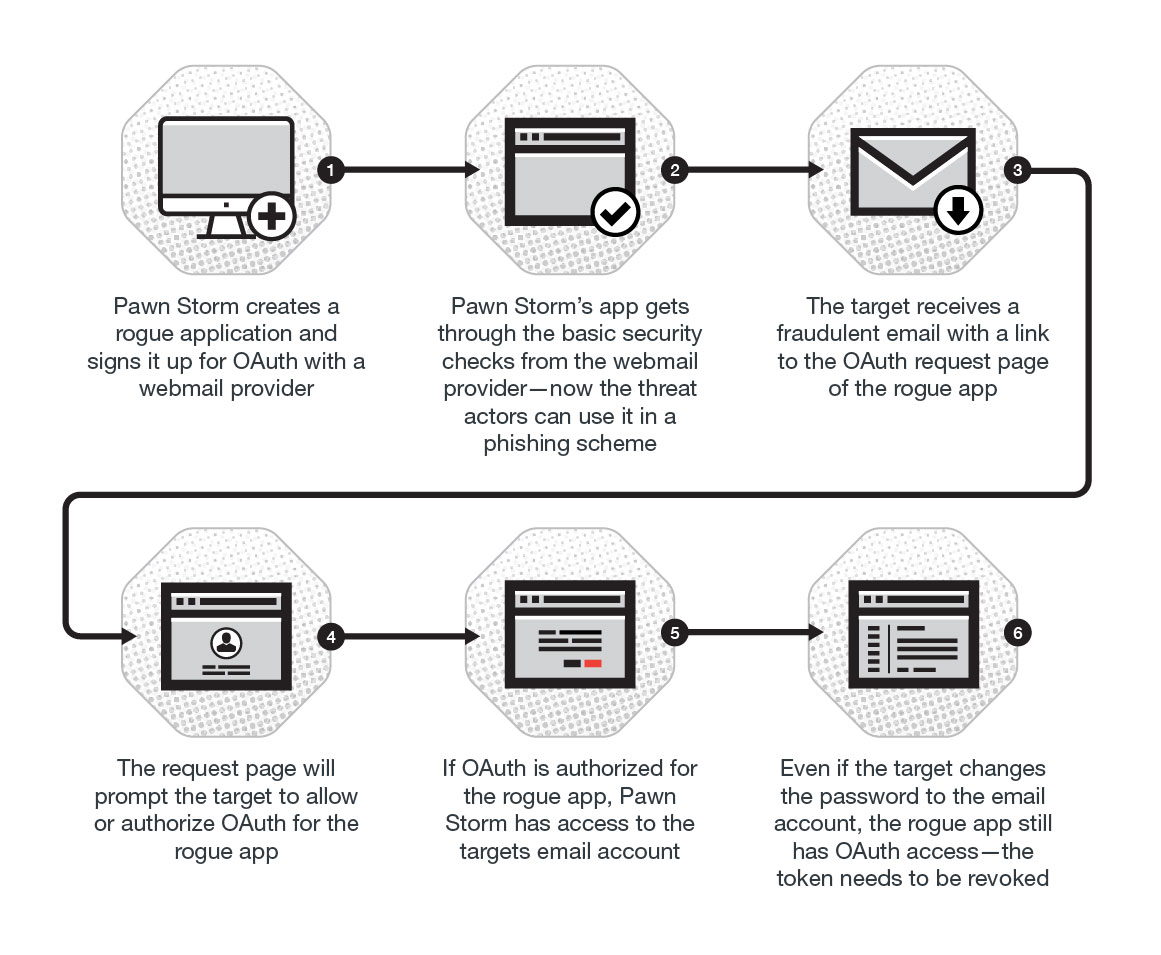
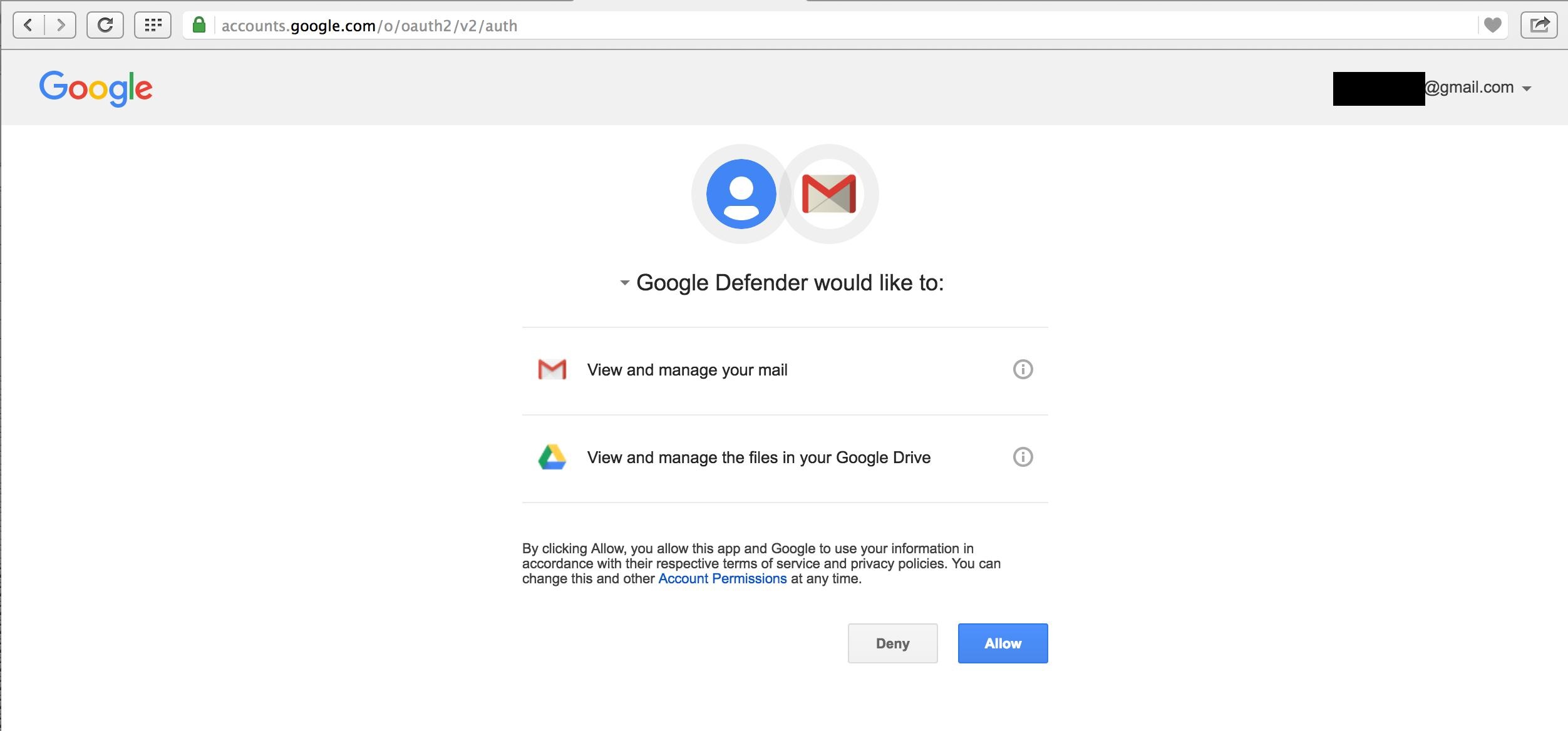
This blog post discusses how Pawn Storm abused Open Authentication (OAuth) in advanced social engineering schemes. High profile users of free webmail were targeted by campaigns between 2015 and 2016.
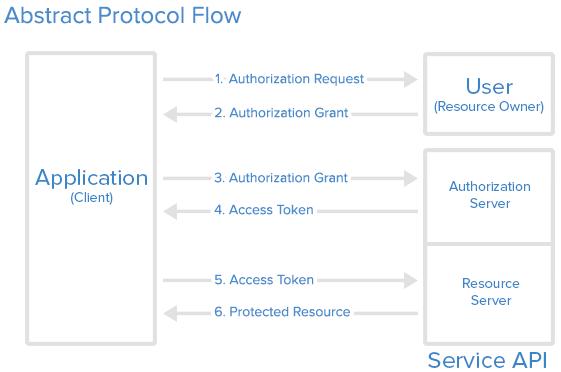
Oauth Token Stealing - Red Team Blog
Pawn Storm Abuses OAuth In Social Engineering Attacks

OAuth, Breaking Cybersecurity News
DEF CON 29 - TIB AV-Portal

OAuth, Breaking Cybersecurity News

Mandiant identifies 3 hacktivist groups working in support of Russia
Must Read - Security Affairs
DEF CON 29 - TIB AV-Portal
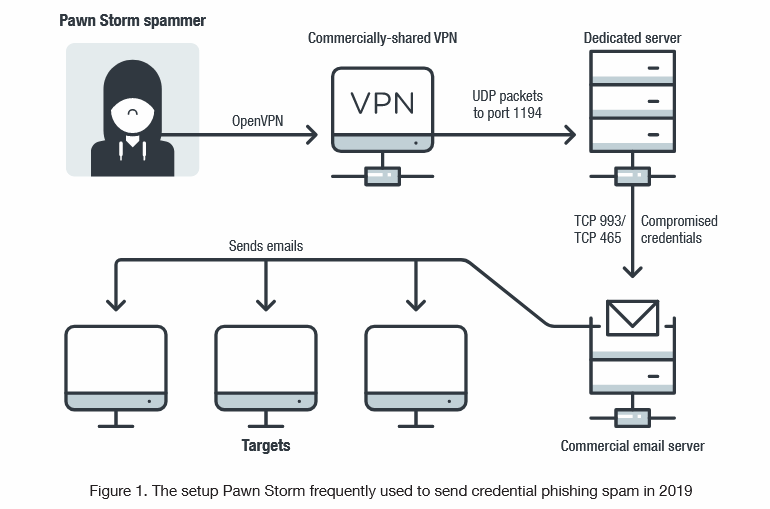
APT28 Archives - Page 2 of 8 - Security Affairs

The 13 Most Common Types of Social Engineering Attacks + How to Defend Against Them
DEF CON 29 - TIB AV-Portal
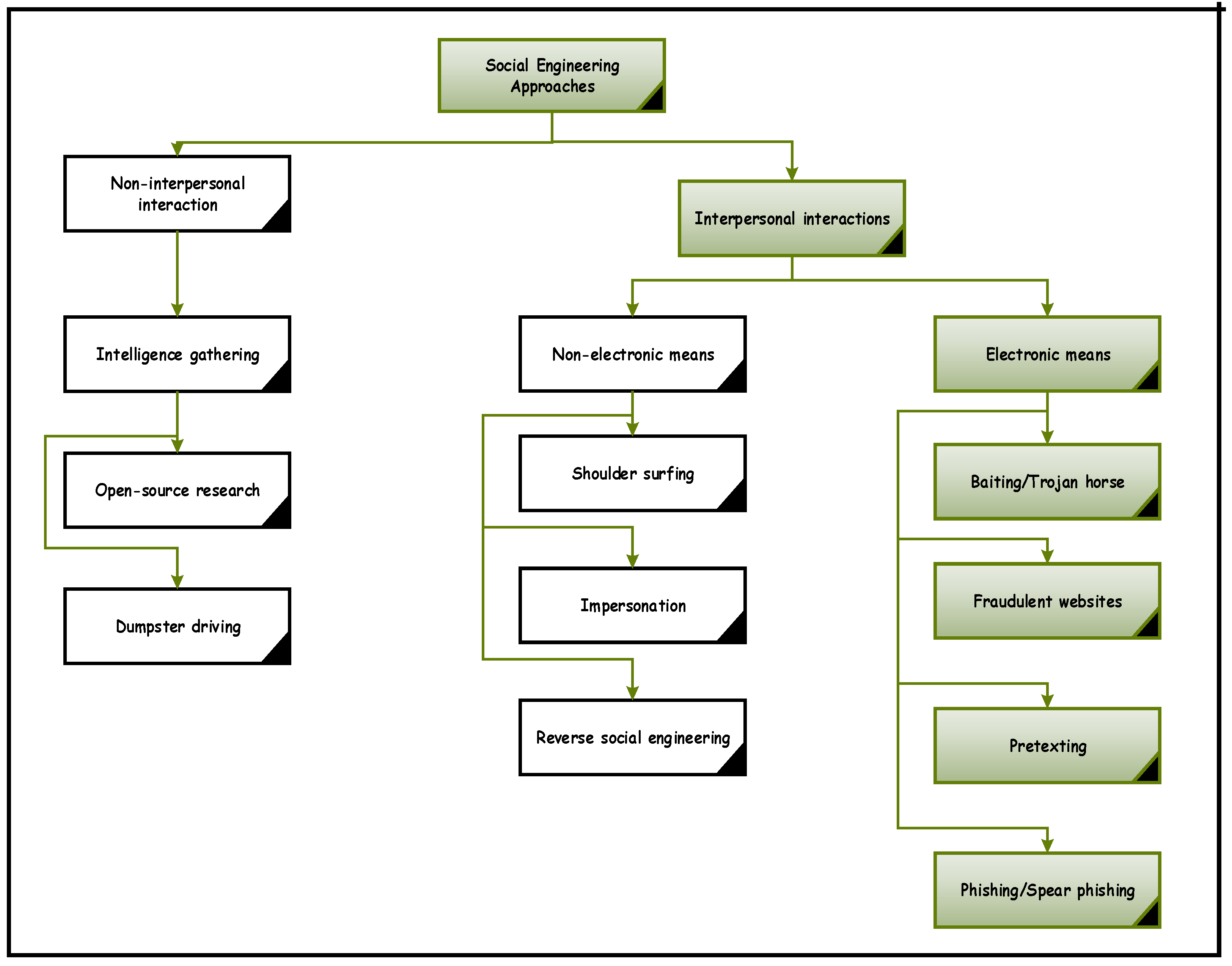
Information, Free Full-Text

TrustedSec Practical OAuth Abuse for Offensive Operations – Part 1

APT28 relies on PowerPoint Mouseover to deliver Graphite malware
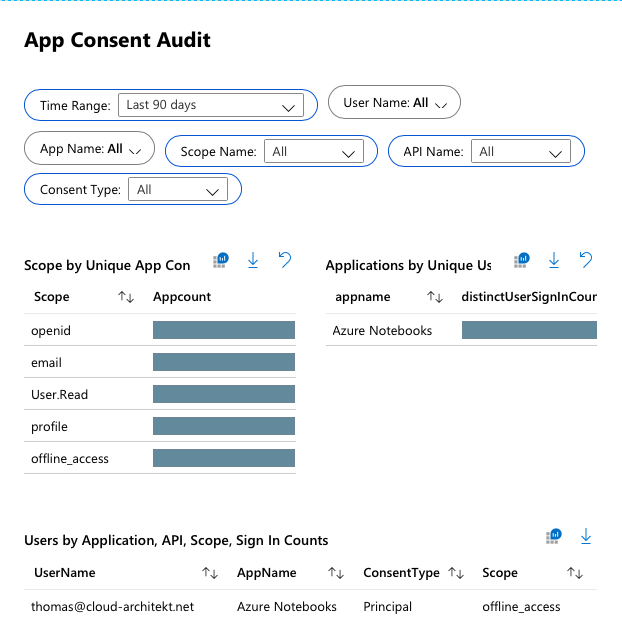
Detection and Mitigation of Illicit Consent Grant Attacks in Azure AD - Thomas Naunheim
Recomendado para você
-
 Pawns.app failed to start, What is this? How do I fix it? : r/Pawnsapp23 maio 2024
Pawns.app failed to start, What is this? How do I fix it? : r/Pawnsapp23 maio 2024 -
 Retail Moblie Apps Bravo Store Systems23 maio 2024
Retail Moblie Apps Bravo Store Systems23 maio 2024 -
 Residential Proxy IP Networks: What Everyone in Ad Tech Needs to Know - AdMonsters23 maio 2024
Residential Proxy IP Networks: What Everyone in Ad Tech Needs to Know - AdMonsters23 maio 2024 -
 Finn and Israeli Combo Blaze Trail on 'Beverly Hills Pawn' App Tie-In - WSJ23 maio 2024
Finn and Israeli Combo Blaze Trail on 'Beverly Hills Pawn' App Tie-In - WSJ23 maio 2024 -
 Pawns App Review - New, Ultimate and Comprehensive23 maio 2024
Pawns App Review - New, Ultimate and Comprehensive23 maio 2024 -
 Pawn Shop Map Announces App To Connect Pawn Shops With Customers Nearby23 maio 2024
Pawn Shop Map Announces App To Connect Pawn Shops With Customers Nearby23 maio 2024 -
 Earn Money By Sharing Your Internet With Pawns.app? (Review)23 maio 2024
Earn Money By Sharing Your Internet With Pawns.app? (Review)23 maio 2024 -
 MerryIoT Light Hotspot, Helium Miner, Multi Mining, LoRaWAN Gateway, Hotspot, Crypto Mining, HNT, Mysterium, Honeygain, Pawns and Traffmonetizer : Electronics23 maio 2024
MerryIoT Light Hotspot, Helium Miner, Multi Mining, LoRaWAN Gateway, Hotspot, Crypto Mining, HNT, Mysterium, Honeygain, Pawns and Traffmonetizer : Electronics23 maio 2024 -
Hands-On Equations 1 - Microsoft Apps23 maio 2024
-
Pawns.app on LinkedIn: Finance Terms 101 - Definitions Everyone Should Know - Pawns23 maio 2024
você pode gostar
-
 Anime Review: Vlad Love23 maio 2024
Anime Review: Vlad Love23 maio 2024 -
 Comprar Rayman Legends - Ps5 Mídia Digital - R$29,90 - Ato Games23 maio 2024
Comprar Rayman Legends - Ps5 Mídia Digital - R$29,90 - Ato Games23 maio 2024 -
 Easy Gluten-Free Soft Pretzels –23 maio 2024
Easy Gluten-Free Soft Pretzels –23 maio 2024 -
 Clannad Collector's Edition Unboxing23 maio 2024
Clannad Collector's Edition Unboxing23 maio 2024 -
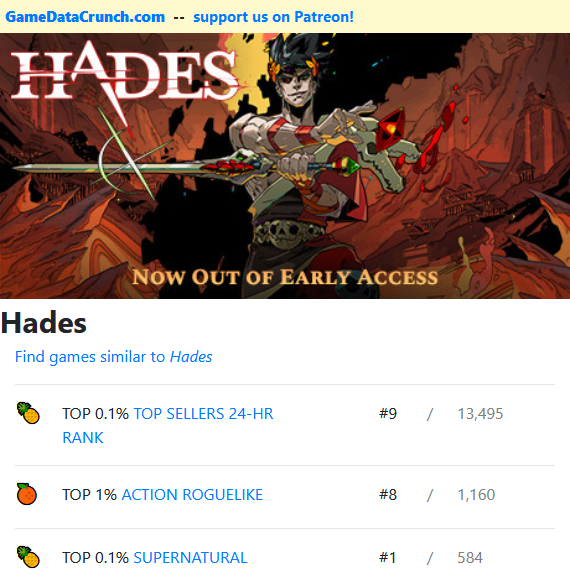 GameDataCrunch: my facts-first game metrics website23 maio 2024
GameDataCrunch: my facts-first game metrics website23 maio 2024 -
 Kasparov se torna o mais jovem campeão mundial de xadrez23 maio 2024
Kasparov se torna o mais jovem campeão mundial de xadrez23 maio 2024 -
 The LEGO Batman Movie: Harley Quinn Cannonball Attack (70921) Toys23 maio 2024
The LEGO Batman Movie: Harley Quinn Cannonball Attack (70921) Toys23 maio 2024 -
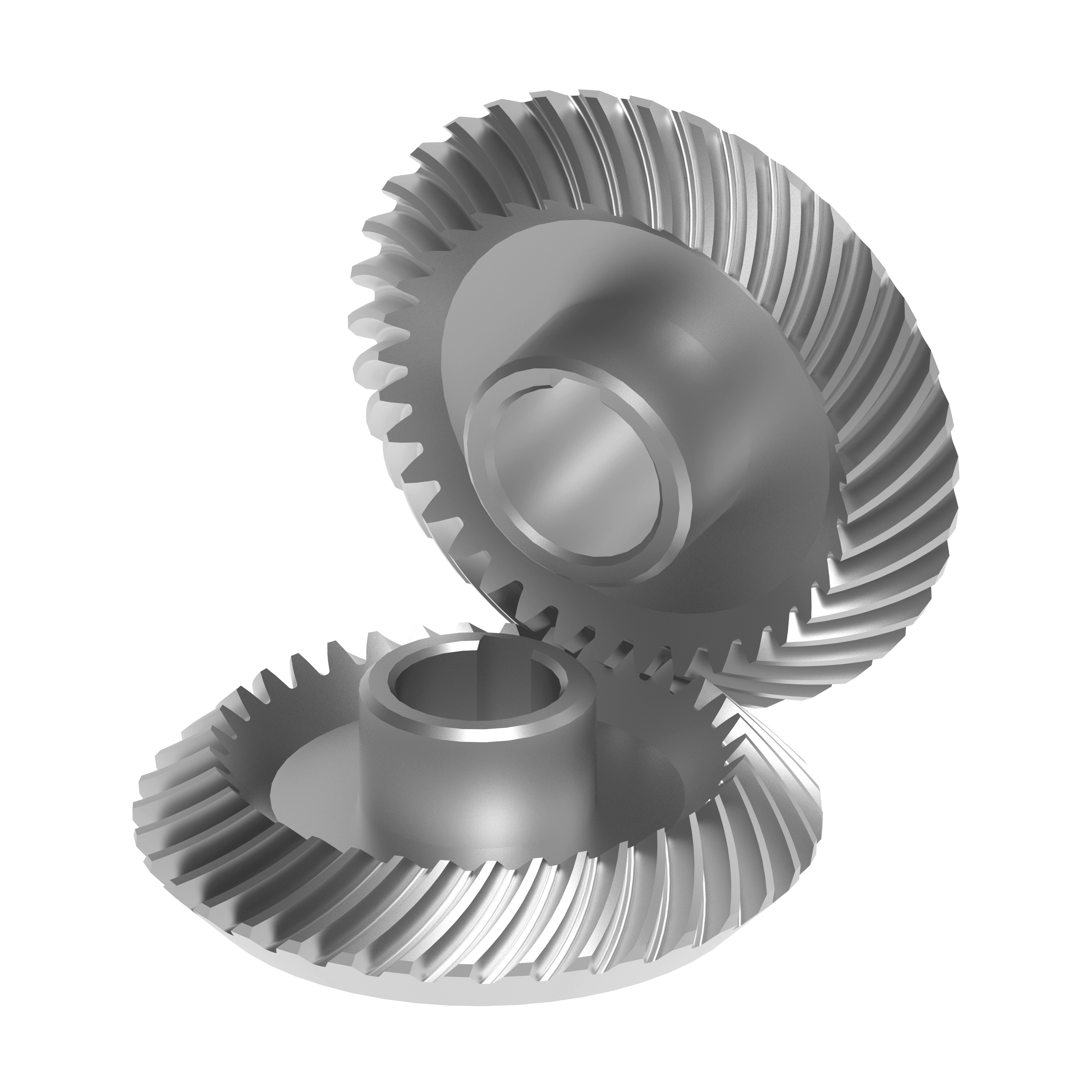 Miter Gear - 3D model by Roboninja on Thangs23 maio 2024
Miter Gear - 3D model by Roboninja on Thangs23 maio 2024 -
 CLANNAD (クラナド) - Yukine Miyazawa (宮沢 有紀音)23 maio 2024
CLANNAD (クラナド) - Yukine Miyazawa (宮沢 有紀音)23 maio 2024 -
Register for #Autophagy and Disease on Dec. 3-6 in Keystone, CO23 maio 2024


